Search Results
Showing results 1 to 10 of 10

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.

Color by Numbers: Image Representation
Source Institutions
Computers store drawings, photographs, and other pictures using only numbers. Through this activity, learners decode numbers to create pictures using the same process that computers use.

Programming Languages: Marching Orders
Source Institutions
In this activity about computer programming, learners follow instructions in a variety of ways in order to successfully draw figures.
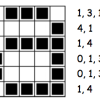
Colour by Numbers: Image Representation
Source Institutions
This activity shows learners how computers use numbers to represent pictures. A grid is used to represent the pixels (short for picture elements) of a computer screen.
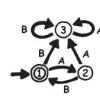
Treasure Hunt: Finite-State Automata
In this computer science activity about finite-state automaton (on page 45 of the PDF), learners use a map and choose various pathways to find Treasure Island.
Solving Playground Network Problems
Source Institutions
In this activity, learners use cooperation and logical thinking to find solutions to network problems on the playground.

Binary Challenge
Source Institutions
In this activity, learners cut out 5 paper cards and label them with 1, 2, 4, 8, or 16 dot(s) to explore binary digits.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.

The Orange Game: Routing and Deadlock in Networks
Source Institutions
When a lot of people share one network (such as cars using roads, or messages getting through the Internet), there is the possibility that competing processes will create a “deadlock," or an interrupt

Information Hiding: Sharing Secrets
Source Institutions
This activity about cryptographic techniques illustrates a situation where information is shared, and yet none of it is revealed.
